Zero Trust Approach
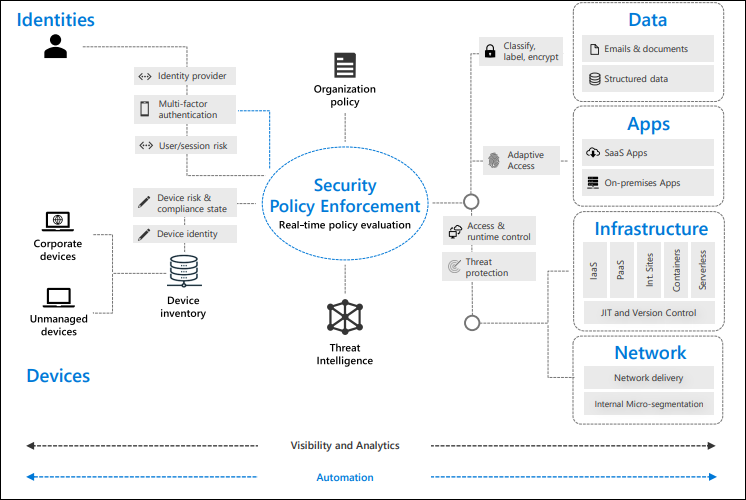
A Zero Trust approach should extend throughout the entire digital estate and serve as an integrated security philosophy and end-to-end strategy. This is done by implementing Zero Trust controls and technologies across six foundational elements: Identities, Devices, Applications, Data, Infrastructure, and Networks. Each of these six foundational elements is a source of signal, a control plane for enforcement, and a critical resource to be defended.


